Secret Key Algorithms in Cryptography
Cryptography
Cryptography is basically both the practice and the study of hiding information. It has worked to protect confidential documents for decades. Today, cryptographic techniques of the modern day are used in several ways to ensure safe communication. Authentication, integrity, and confidentiality are components of cryptography.
Symmetric Key Algorithms
Symmetric key algorithms also known as secret key algorithms because these algorithms basically use one & only key in the encryption and decryption processes by both the involving parties. When compare to the asymmetric key algorithms, symmetric key algorithms are more secure and very fast. Secret key algorithms are basically used in the places where that needs to encrypt lot of data.
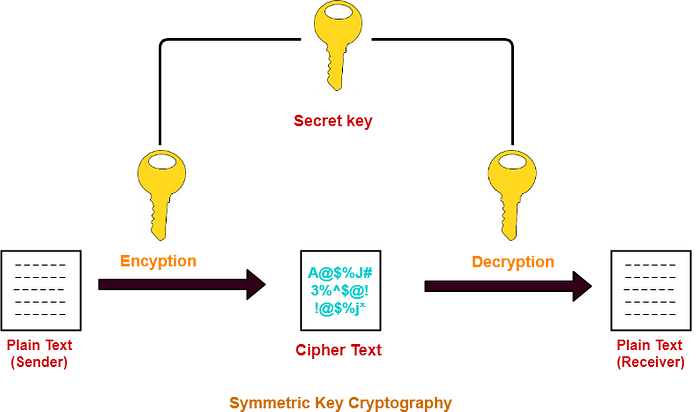
There are about hundreds of different symmetric key algorithms. In this article I’ll demonstrate some common symmetric key algorithms.
DES
DES is the Data Encryption Standard. It has developed in 1976 and this was one of the most commonly used algorithms for the encryption.This is in part because it was adopted as the government encryption standard. The DES algorithm is very powerful in itself. DES is a block cipher, which encrypts data into blocks of 64 bit size each, meaning that 64 bits of plain text goes as the DES input, which produces 64 bits of cipher text. For encryption and decryption the same algorithm and key is used, with slight variations. The vulnerability lies in the fact that a 56-bit encryption key is used in the original DES format. When compare to the period that DES was developed, modern computers are much faster so they can run through all the combinations of the key. Though DES is not commonly used anymore.

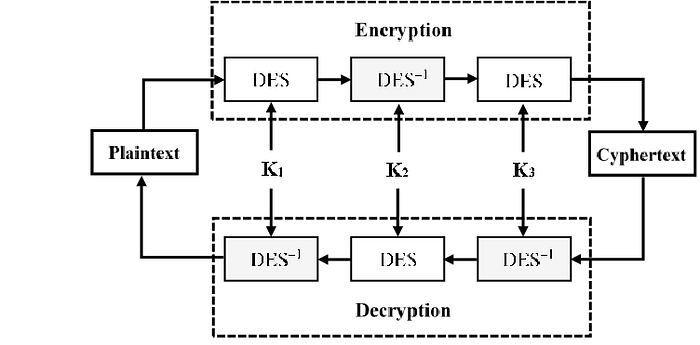
3DES
This is also known as Triple DES. 3DES gets its name, since the DES algorithm is applied three times to each data block. 3DES has overtaken its predecessor, DES, and is considered the most commonly used standard for secure encryption at this time. The algorithm itself is just as efficient as DES but it has the benefit of that can use longer key lengths. For each of the 3DES encryption iterations a key has to be specified. For each, it has the choice to use the same key, the same for two of the iterations, or a different key for each iteration. The most reliable implementation is for every iteration to use a different key. When all three iterations use the same main, the main force is considered to be 56 bits. Essentially, this is the same as DES. If the same key is used for two of the iterations and a different key for the third, then 112 bits are known to be the key power. When all three iterations use a different key, then the encryption strength is considered to be 168 bits.
AES
AES is the Advanced Encryption Standard. Indeed, the AES format contains three distinct ciphers: AES-128, AES-192, and AES-256. The numbers show the duration of the encryption key. AES is very fast and very healthy. Regardless of that, its global take-up was very fast.

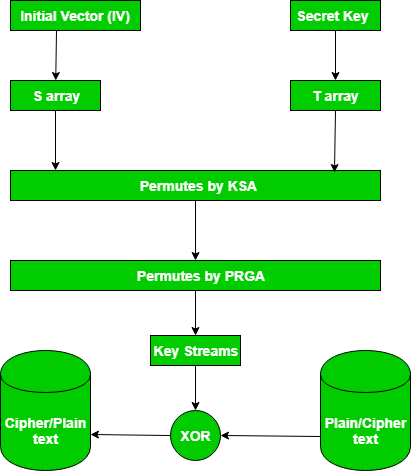
RC4
It is the fourth version of Rivest Cipher. RC4 uses an encryption key of variable length. The key can vary between 40 and 256 bits. It is most widely used with 128-bit token. The RC4 algorithm is easy to implement and is very basic. The concern is that if poorly applied, this can result in poor cryptographic systems. It is one of the key reasons for the late phasing-out of RC4. RC4 was one of the most commonly used algorithms for the encryption.
RC5
It is the fifth Rivest Cipher edition. RC5 is a block cipher which addresses two blocks of words at once. It is simple, fast and consumes less memory. RC5 uses encryption keys of variable frequency. They can span as much as 2040 bits. The key size suggested for this is 128 bits.

Following table shows key length and block size for above described algorithms.

In this post I have demonstrated some common symmetric key algorithms in cryptography. My next post is on public key algorithms in cryptography.
